


Next: Chapter 27
Up: Notes on ``TCP/IP Illustrated''
Previous: Chapter 25
- p. 392
- The recommendation against using .rhosts files is
certainly as valid now as then. Especially in Universities (and Bath is no
exception), a Kerberos-based system is used instead.
- p. 395
- The comparison between client
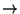 server signalling
and server
server signalling
and server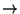 client signalling is not quite as clear (in my
opinion) as Stevens makes out. In particular, Telnet uses
(essentially)52 in-band in both directions, but has a true escape mechanism,
whereas rlogin does not have a way of sending the escape character 0xff as data.
client signalling is not quite as clear (in my
opinion) as Stevens makes out. In particular, Telnet uses
(essentially)52 in-band in both directions, but has a true escape mechanism,
whereas rlogin does not have a way of sending the escape character 0xff as data.
- p. 398
- Logically (especially in the context of large fat networks),
step 8 need only follow step 2, but in a LAN context (where rlogin is
normally used) it will follow step 7.
- pp. 401-3
- telnet is fundamentally trying to solve a
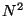 problem:
if there are
problem:
if there are 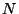 different kinds of terminal, there are
different kinds of terminal, there are 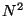 possible
mappings. Mapping to/from NVT makes it a
possible
mappings. Mapping to/from NVT makes it a 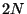 problem, but at the cost of
crippling some functionality/response, so a compromise has to be sought.
This explains the graph of code size in Figure 26.1
problem, but at the cost of
crippling some functionality/response, so a compromise has to be sought.
This explains the graph of code size in Figure 26.1
- Figure 26.13
- Segments 7 and 8 have, due to the delayed ACK rule, a
20% chance of being combined. So an option can be acknowledged at the same
time as it is being replied to, but the TCP client cannot see this.
- p. 413
- Of course, if the Nagle algorithm is disabled, then every
character typed is sent in a separate segment.



Next: Chapter 27
Up: Notes on ``TCP/IP Illustrated''
Previous: Chapter 25
James Davenport
2004-03-09